
Managing cloud security is no easy task; security operations teams have to actively identify emerging threats before they escalate by analyzing log data. That’s where AWS GuardDuty comes in: an AWS feature that analyses logs and events from various data sources such as CloudTrail logs, compute instance workloads, DNS logs, VPC logs, and more. It takes threat detection to the next level with machine learning algorithms and threat intelligence to identify patterns indicative of malicious activity. Let’s dive into what does AWS GuardDuty do and why it’s an important feature to add to your cloud management.
What is AWS GuardDuty?
AWS GuardDuty is a managed threat detection service that provides 24/7 monitoring of your AWS environment for potential security threats and malicious activity. GuardDuty uses machine learning, anomaly detection, and integrated threat intelligence to identify and alert you on where your attention is needed to reduce the risk of threats. It is a valuable tool that saves time analyzing account-level security levels.
How does Amazon GuardDuty work?
AWS GuardDuty works by continuously monitoring and analyzing activities and behaviors in your AWS environment to detect potential security threats. It collects data from a variety of sources within your AWS environment. This data is preprocessed to extract relevant information, such as source and destination IP addresses, user identities, and the type of AWS resource involved. Using Machine Learning algorithms, this data is efficiently analysed to see if there are any changes to what is standard. An example of this would be a particular user attempting to access resources they’ve never tried before.
Along with continuous monitoring, GuardDuty leverages threat intelligence feeds from AWS, as well as industry-standard sources, to identify known attack patterns, malicious IP addresses, and domains. It cross-references the data it collects with these threat intelligence feeds to spot signs of malicious activity.
With this flow of information, if it detects suspicious activities, and it generates findings. These are essentially security alerts that provide information on the potential threat and the recommended next actions to take.
How to deploy GuardDuty manually?
To manually enable GuardDuty, here’s what you need to do:
- In the AWS Management Console, go to the “Services” menu and select “GuardDuty” under the “Security, Identity, & Compliance” category.
- Click on “Enable GuardDuty” to activate the service for your AWS account. You will be prompted to choose a region for enabling GuardDuty.
- GuardDuty requires a designated Amazon S3 bucket to store findings and related data. You can create a new S3 bucket or select an existing one for this purpose.
- Review your choices and configurations, and then click “Save” to enable GuardDuty in your chosen region.
- You can customize GuardDuty settings, such as enabling CloudTrail and VPC Flow Logs integration, setting up organizational units, and adjusting the frequency of findings.
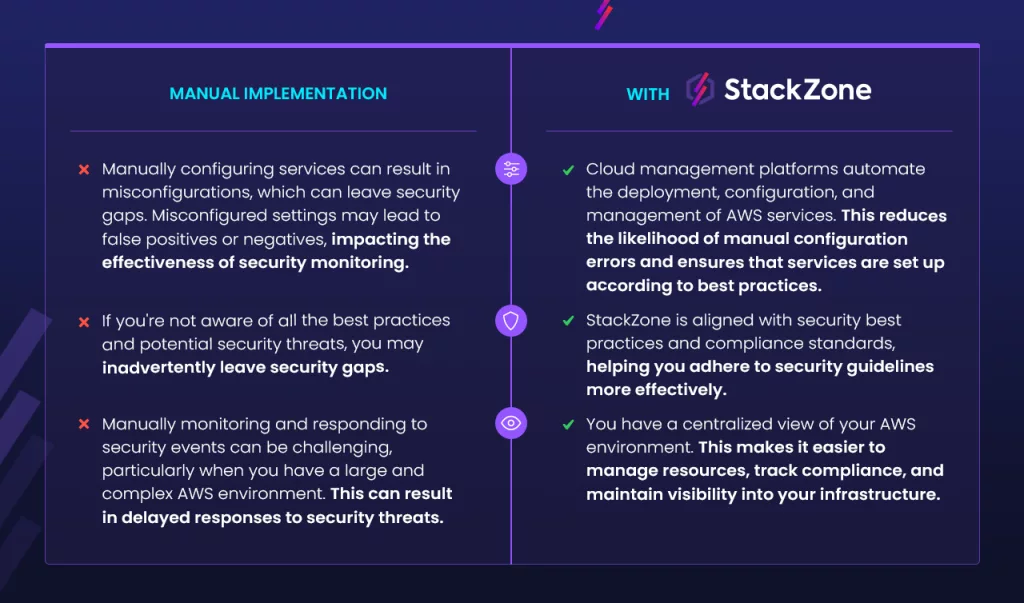
Should I manually enable GuardDuty or use a cloud management platform?
While you have the option of using AWS GuardDuty yourself, there are benefits to your cloud management when you rely on an AWS cloud management platform, like StackZone:
Use cases of AWS GuardDuty
Continuous threat detection
GuardDuty provides continuous threat detection by monitoring AWS environments for suspicious activities, swiftly identifying potential security threats, and generating real-time alerts.
Malicious IP detection
AWS GuardDuty identifies and notifies you about traffic from malicious IP addresses and domains, aiding in the prevention of potential attacks and safeguarding your resources.
Anomalous behavior detection
GuardDuty employs machine learning to establish a baseline of “normal” behavior in your AWS environment, promptly generating findings when deviations occur, enabling the detection of potential security breaches and providing insights into compromised credentials and suspicious logins.
Integration with other AWS services
GuardDuty seamlessly integrates with various AWS services, such as AWS CloudWatch, AWS Lambda, and Amazon S3, allowing for automated responses to security events and the establishment of efficient incident response mechanisms based on specific findings.
The benefits of Amazon GuardDuty
Saves you time with its intelligence
AWS GuardDuty can analyze an extensive volume of events per second, ranging in the tens of billions, sourced from various AWS data channels. You don’t need to manually collect and analyse masses of data from multiple accounts.
Provides context to suspicious activity
Within your AWS accounts, Amazon GuardDuty identifies uncommon actions, evaluates their security importance, and provides contextual information. This enables a responder to determine if further investigation is required.
Prevents the risk of a security breach
The threat detection capabilities of AWS GuardDuty and the fact it monitors 24 hours a day means the powerful feature is working hard to protect your AWS environment when your attention isn’t fixed on it.
Helps you to prioritize your next steps
AWS GuardDuty offers three severity levels to help customers decide how to prioritize their response to potential attacks.
- A “Low” severity designation indicates that suspicious or malicious activity was detected but prevented from harming your resources with automation.
- A “Medium” severity level signifies questionable behavior, like an unusual volume of traffic routed through the Tor network or activity that doesn’t conform to the expected norms.
- A resource labeled with “High” severity has been compromised and is currently being exploited for malicious purposes, such as an Amazon EC2 instance or a collection of IAM user credentials. This needs urgent attention to solve.
Always available so you’re protected as you scale
GuardDuty enhances its detection capability when needed and reduces usage when it’s no longer necessary. So as you scale, GuardDuty scales with you.
How does StackZone take AWS GuardDuty further?
Using the cloud management platform, StackZone, you can simplify managing the security of your AWS environments. Our platform reduces the human effort required to get what you need from the cloud. That’s why, every deployment of StackZone results in compliance with security best practices; these best practices are built into the foundation of the software. In the context of AWS GuardDuty, StackZone enhances the feature further with:
A deployment of GuardDuty in all of your accounts
Any new account you create also gets invited to the centralized Amazon GuardDuty detector, so there’s no need to do it manually each time. StackZone ensures you’re fully covered, providing your Security Operations team with full visibility of findings. These findings are aggregated in one tool alongside your other key cloud management metrics such as your compliance score, budget control function, log history and more, saving you time trying to locate each piece of information. You can enable or deactivate features, config rules and remediations in a single click such as CloudWatch alarms and Single Sign On (SSO) tags, all contributing to a decreased security risk level.
GuardDuty remediations
StackZone’s GuardDuty remediations protect your VPC network and EC2 instances. Essentially, when threats are detected, StackZone’s enablement of GuardDuty means it can instantly react before you even notice the threat! Security requires a proactive approach which is why our team expertly built the remediations to always be one step ahead to prevent any harm.
The remediation works to protect by the ongoing collection of findings which StackZone monitors 24/7. When our security tool detects a threat, through your findings, it automatically reacts.
GuardDuty remediations will protect your VPC networks and EC2 Instances from additional potential attack threats and vectors. When we receive particular GuardDuty findings which could be an attack on one of your instances, we take action by blocking the attacker’s source IP within the VPC network with the creation of ACLs (Access Control Lists) that explicitly refuse incoming traffic originating from that particular source IP address.
AWS GuardDuty notifications
StackZone takes the AWS feature of GuardDuty further with advanced notifications. These are core account features which we can build for you inside your Security Account. Each notification can be triggered on or off depending on what you feel your cloud security needs for your business requirements.
To enable these and choose what notifications you want to receive, head on over to the StackZone Console and under “provisioning”, head to Core Accounts. From here choose the Security Account and select the subpage GuardDuty. Four examples of when these notifications are triggered include:
- CloudTrail trail within your AWS environment was disabled – Such an action may be an attacker’s effort to disable logging in order to obscure their actions and erase any evidence of their unauthorized access to your AWS resources for malicious intent. This event would need your attention and priority because they are operating invisibly in your accounts. Without the advanced notification, the hacker could go much further into your accounts.
- A weak password has been created or deletion of your AWS account password policy- If a user chooses a weak password that is simple to recall and potentially more vulnerable to guessing, a security threat has been created. This notification allows you to ensure they’re strong passwords implemented for all users, leaving no room for risk. You could also receive this notification if someone has attempted to update or delete your password policy which is highly suspicious behavior and would need urgent investigation. Without this notification, it could be days, weeks, or longer till you notice your password policy is no longer in place.
- An EC2 instance is trying to connect to multiple ports – This finding would indicate that the specified EC2 instance within your AWS setup is involved in a potential port scanning attack. It’s attempting connections to multiple ports within a brief timeframe. The intention behind a port scan attack is to identify open ports, determine the services running on the target machine, and ascertain its operating system.
- Unusual traffic for EC2 – This discovery alerts you that the mentioned EC2 instance in your AWS environment is exhibiting behavior that differs from the expected norm. Specifically, this instance has no prior record of sending such a significant volume of traffic to the specified remote host. This could indicate the presence of a hacker.
AWS GuardDuty FAQs
What is the difference between AWS GuardDuty vs Amazon Macie?
Amazon Macie is a data security and privacy service designed to automatically discover, classify, and protect sensitive data within AWS, aiding in compliance and data protection. While GuardDuty emphasizes threat detection and monitoring, Macie is geared toward data discovery and protection, often used for regulatory compliance and data privacy needs.
Is AWS GuardDuty available in all AWS regions?
AWS GuardDuty is available in many AWS regions, but not all. You should check the official AWS Regional Services List to confirm its availability in your specific region. AWS typically continues to expand service availability to additional regions over time.
Does AWS GuardDuty have a free trial or a free usage tier?
You have the offer of a 30-day free trial that includes 30 days of data retention. After the trial, you will be billed based on the volume of data analyzed and the findings generated. To achieve cost visibility and optimization, StackZone can notify you when your free trial is up and ensure you’re not spending any more than you should be.
Can GuardDuty be used in conjunction with other AWS security services?
Yes, AWS GuardDuty can be integrated with other AWS services like AWS CloudWatch, AWS Lambda, and AWS S3. This integration allows you to automate responses to security findings, making your incident response more efficient and allowing for custom remediation actions.
What is the difference between AWS GuardDuty vs AWS Shield?
AWS Shield is a managed Distributed Denial of Service (DDoS) protection service designed to safeguard applications running on AWS from DDoS attacks, ensuring high availability and minimal disruption. While GuardDuty focuses on threat detection, Shield is primarily concerned with protecting against DDoS attacks.
Is GuardDuty a regional service?
Yes, GuardDuty is a regional service. If your workloads runs on a multiaccount/multiregion environment GuardDuty should be deployed on every region and account. StackZone simplified this by deploying GuardDuty on every region and account and centralizing its findings and management into the security account.
Are GuardDuty auto remediations deployed by default?
No, GuardDuty autoremediations must be developed and deployed separately. StackZone does this by simply activating the feature on the console. In that way, your VPC Networks and EC2 instances will be protected against additional potential attack threats and vectors.
Summarizing AWS GuardDuty
If you’re looking to strengthen your security posture in a way that’s simple to deploy and straightforward to manage, then AWS GuardDuty keeps you in control of threats as they begin to emerge. StackZone is the security tool for you because it simplifies the deployment and management of AWS GuardDuty (along with hundreds of other security features) but also increases the protection you receive with remediations, automation of deployment across all accounts, advanced notifications, and complete visibility. Why not see for yourself? Book a demo and one of our experts will show just how transformative the StackZone platform is.
This article was written by Ryan Ware, DevOps Engineer Consultant
