Following AWS identity and access management best practices should underpin all security activities in your cloud infrastructure. This article will explore the Zero Trust model, identify different types of users, and outline the best practices for identity and access management so you can transform your risk level and keep your business safe. By implementing the following best practices you can also expect your overall cloud management to simplify, saving you lots of time to invest into your business tasks.
What is cloud identity and access management?
AWS Identity and Access Management (IAM) is essential for cloud security. A set of practices are needed to govern the management of user identities and their access to resources within an organization’s information systems and cloud services. These best practices for identity and access management allows you to securely scale without open vulnerabilities.
In simple terms, cloud identity and access management are all about ensuring that only the right profiles access your infrastructure and information in the cloud. This controls the capabilities of their actions; they can only do what they should in alignment with what their role is. To increase your AWS cloud security, your cloud identity and access management strategy must ensure:
- Minimum privileges
- Restricting actions as much as possible
- Identification of the user and/or role through multiple methods
- Temporary credentials
The impact of identity and access management on your cloud security
Cloud security requires a holistic approach. Essentially, you need to cover all bases and ensure you’re protecting every part of your cloud infrastructure. Using AWS identity and access management best practices provides great progress for reducing your risk level because it provides user accountability, resource isolation, and the least privilege principle. It’s important to not rely on any one single approach, person in your team, or automation to manage your cloud security. Once you’ve introduced the AWS identity and access management best practices, you can take this further with an alerting strategy and tagging.
The types of users you need to manage access for
When aiming to operate secure AWS workloads, you need to be aware of the different types of users. Understanding each of them helps you guarantee that the correct identities only have access to the resources they need, under the right conditions. IAM deals mainly with four principal entities: users (humans), groups, machines, and policies. These 4 categories detail who a user is and what that user is allowed to do within the environment. Let’s break these down:
Human users
In the context of identity and access management, human users are sometimes referred to as human identities. A user is any person in your internal organization or an external collaborator who interacts with your AWS resources via web browser, client application, or interactive command-line tools. These are your administrators, developers, operators, and end-users who require an identity to access AWS environments and applications. Typically, human users will be provided with authorization credentials, such as a username and password, to verify their identity. It’s a cloud best practice to use Multi-Factor Authentication. Once authenticated, users are granted access to specific resources based on assigned permissions or policies.
It’s crucial to view the people who have access to your infrastructure as “users” as opposed to individuals so you can pinpoint what their duties are and consequently what permissions and access they need. This prevents you from providing too much access to someone just because you’ve worked together for years, for example.
Policies
Policies in AWS are entities linked to users, groups, roles, or resources, dictating the permissions granted to those entities. When a user seeks access to a resource, their request is matched against the relevant policies. If the request is allowed, access is granted; otherwise, it’s denied. AWS policies rely on six criteria: identity, resources, permission boundaries, service control policies, access control lists, and session policies. IT teams have the flexibility to assign multiple policies to each identity, ensuring precise and detailed control over permissions.
Groups
In the context of access management, a group is a gathering of users who share common permissions and policies. When permissions are assigned to a group, all users within that group automatically inherit those permissions. For instance, if a user is placed in a developer group, they will immediately receive all the permissions associated with what permissions you would provide a developer with manually. IT teams have the flexibility to move users between groups, allowing for seamless automatic adjustment of permissions as groups evolve or change.
Machines
Machine users are granted specific permissions and access rights to perform certain tasks or operations. These include your service applications, operational tools, and workloads that require an identity to make requests to AWS services, for example, to read data. The latter includes machines running in your AWS environment, such as Amazon EC2 instances or AWS Lambda functions.
Some of the AWS identity and access management best practices will just apply to human users, and others will just apply to machines.
12 AWS identity and access management best practices
Let’s dive into the essential best practices for identity and access management that you should introduce to your AWS cloud management to transform your level of cloud security control.
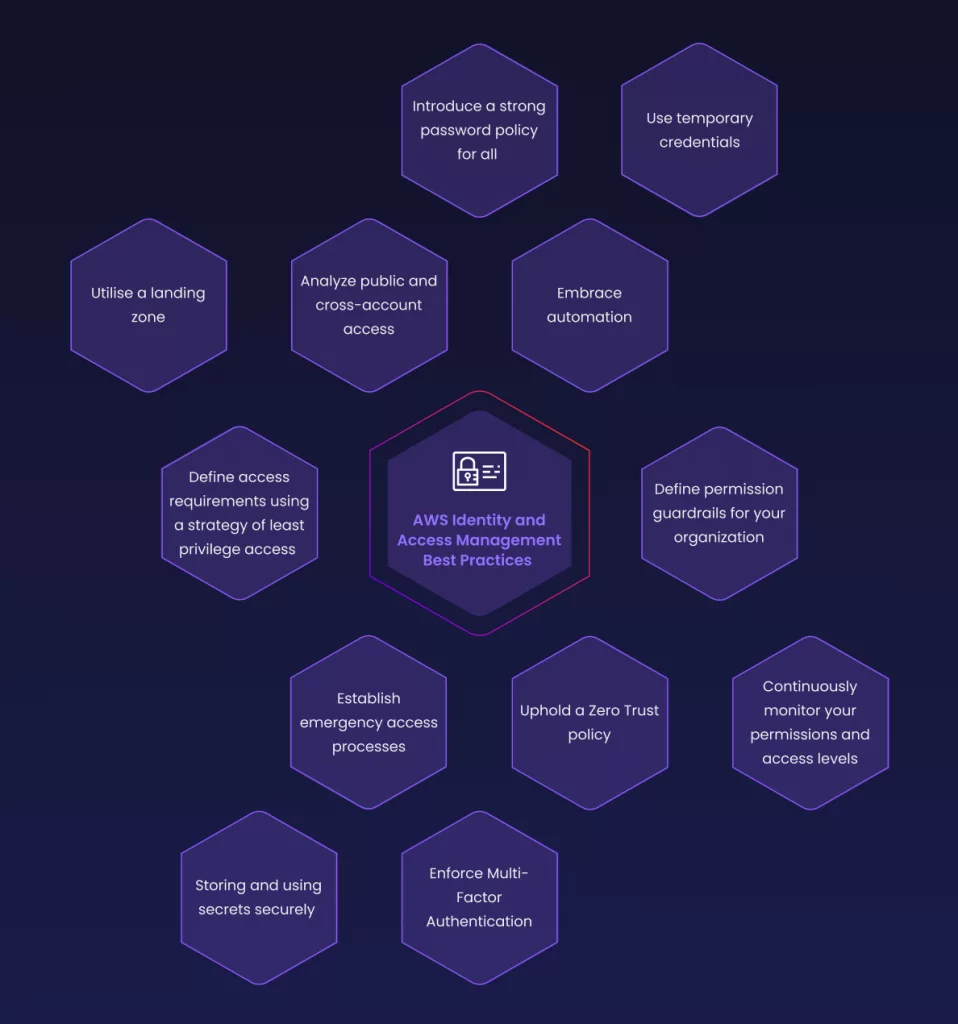
Define access requirements using a strategy of least privilege access
Each one of the components or resources that make up the entirety of your workload needs to be accessed by different parties, such as administrators, end-users, or other components. The first AWS IAM best practice should be to have a clear understanding of who or what needs to have access to each component in your workload. Then, you should choose the appropriate identity type and method of authentication and authorization. You should define resource access and its conditions based on the user’s job function, role, and responsibilities. Grouping users with common requirements together will make the delegation of policies easier.
We recommend you do this with a least-privilege approach. By granting least privilege, each user or machine should only have access to those resources that are absolutely necessary for the performance of their tasks, no more and no less. Take no risks!
Consider AWS permission boundaries. These are advanced features for using a managed policy that sets the maximum permissions an identity-based policy can grant to an IAM entity. An entity’s permissions boundary will be able to ensure the said entity is able to perform only the interactions that are allowed by a combination of their identity-based policies and their permissions boundaries. Lastly, you should consider leveraging tags to control access to any of your AWS resources that support tagging. IAM users and roles can also be tagged to control what they can access.
Uphold a Zero Trust policy
Zero Trust is a security framework and access management approach that never makes allowances for trust and user verification. Many companies have applications, platforms, and tools that are designed with implicit trust features. So users are remembered and don’t have to provide extensive verification each time they use the cloud. Each and every request for access to resources should be authenticated and verified, even for users who are accessing the organization’s network or who have previously had access. This supports you in situations where a user’s credentials have been stolen or a device has been compromised.
Zero Trust security model relies on core principles:
- Always verify before trusting
- Assume breach
- Micro-segmentation
Find out more about implementing a Zero Trust policy.
Establish emergency access processes
In the unlikely event of an emergency, there should be a process in place that allows emergency access to your workload. While you will be relying on least privilege access most of the time, having an emergency access process established will ensure that users can obtain the right level of access when they need it in an emergency situation. The best way to do this is to pre-provision a role for emergency access from a trusted account, for example, one that is in use by the security team. This will help you gain access quickly in a threatening scenario so that you can respond in a timely manner.
Enforce Multi-Factor Authentication
Multi-factor authentication (MFA), should be enforced across your organization to provide an additional layer of security. You can create an IAM policy to enforce MFA sign-in. This will restrict all IAM actions with the exception of those that allow a user to assume roles, change their own credentials, and manage their MFA devices on the My Security Credentials page. You should also enable MFA in your identity provider or single-sign-on service. In addition, you could also configure a strong password policy in IAM and federated identity systems to aid you in protecting against brute-force attacks
Define permission guardrails for your organization
You should establish common controls that restrict access to all identities in your organization. You can, for example, prevent members of your team from deleting common resources. You should take into account your organization’s unique requirements to define common restrictions that apply to every entity in your organization. Find out more about how to do this with AWS Service Control policies.
Introduce a strong password policy for all
While MFA is a hugely important step for reducing unauthorized access, it’s still vital to have strong passwords. The more protection you have, the better! Here are some strong password guidelines:
- Increase the length: Use passwords that are at least 12-16 characters long.
- Complexity: Include a mix of uppercase and lowercase letters, numbers, and special characters (such as !, @, #, $, %, ^, &).
- Avoid predictable patterns: Avoid using easily guessable information like birthdays, names, or common words. Randomness is key.
- Uncommon words: Use words that are not found in the dictionary. You can create a passphrase by combining several unrelated words.
- Avoid personal information: Do not use personal information like your name, username, or any easily discoverable details.
- Don’t use sequences: No sequential or repetitive characters such as 12345 or abcdef
- Never share your password or have the same password for different logins.
- Change your password regularly.
Storing and using secrets securely
The latest industry standards should be used when storing secrets such as passwords to third-party applications that might be used by your team members or machine identities. You can do this by using AWS Secrets Manager, an AWS service that helps you manage items like database credentials, passwords, third-party API keys, and arbitrary text.
Analyze public and cross-account access
You should continuously monitor findings, highlighting public and cross-account access. Only resources that specifically require it, no matter if they are people or machines, should have public or cross-account access. To make sure this is the case, you can use IAM Access Analyzer, which helps you identify the resources in your organization and accounts that are shared with any external entity.
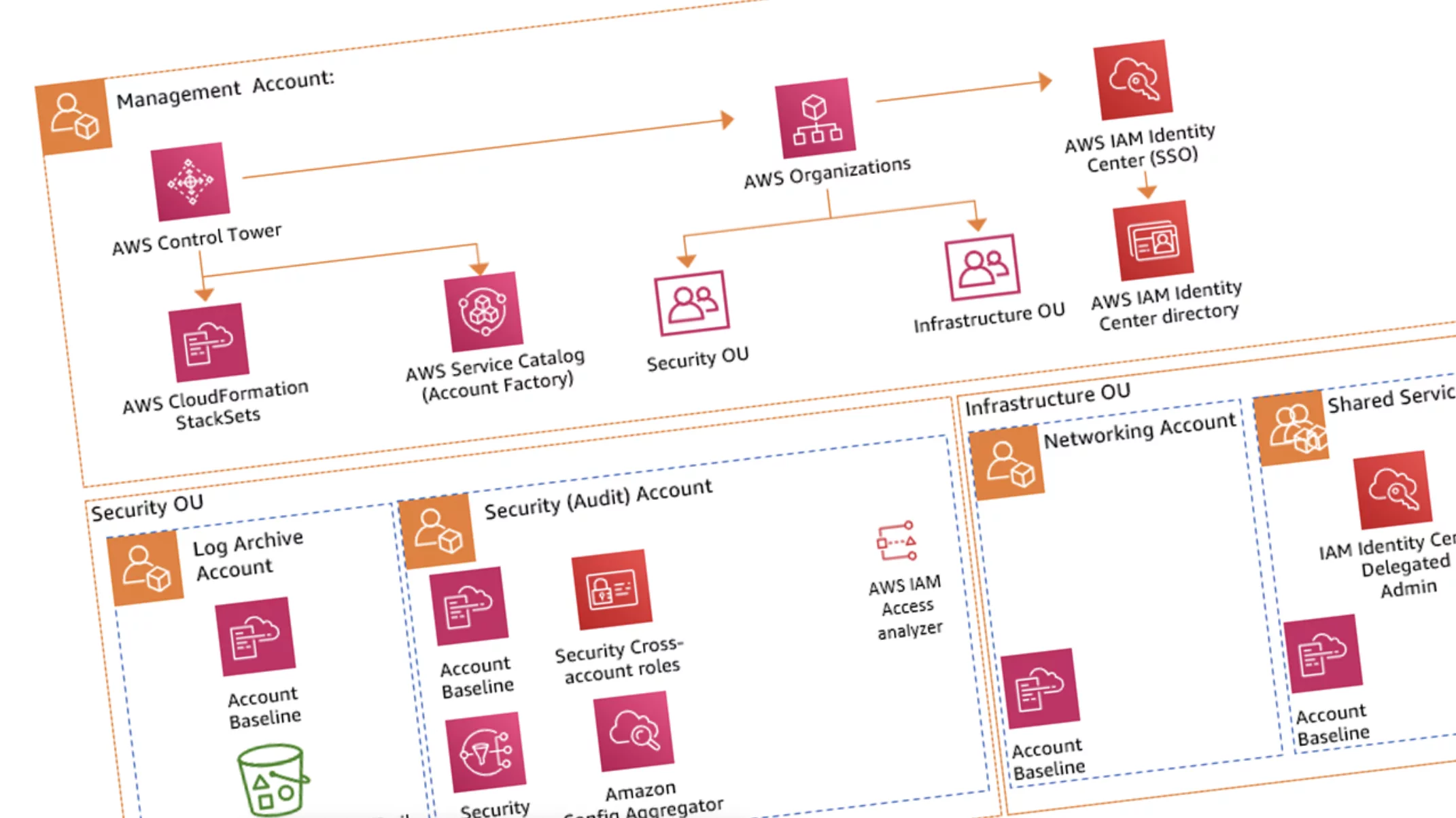
Increase your security boundaries of AWS accounts with StackZone’s landing zone
With StackZone’s landing zones, you inherit all of the security benefits of the AWS landing zone but with increased control and simplified management, powered by automation. The reasons why adopting a multi-account landing zone strategy increases your overall security control are:
- It provides data segregation.
- It provides simple central management for security related day-to-day monitoring and during security incidents.
- It achieves standardization across every environment.
- It provides you with isolated advanced management capabilities for access management, Log management, and security monitoring by defining an specific account for each of them.
Find out more about the importance of landing zones for the cloud.
Embrace automation
Security for the cloud needs to be prioritized 24 hours a day. Automation helps you to stay on top of emerging threats, and access management is no exception. By maximizing your access security, through automation, you can:
- Create standardization – Centrally manage your accesses to ensure every user and role privilege is configured based on your specific organization policy. Implement guardrails through automation in all your environments to ensure they are always accomplished.
- Stay tuned on possible incidents – Security automation will evaluate and send alerts every time a possible incident happens, such as changes in security groups, logging policies, MFA policies, Root user usage, etc.
- Ensure secure access – Monitor and block access to those users and roles that are not compliant with your logging guidelines.
- Prevent unauthorized access – Automation will monitor and ensure all your resources are deployed in accordance with your security policy. Public access removal, password policy monitoring, MFA usage monitoring, and access denial, are all examples of what will be monitories and remediated with automation.
The cloud management platform, StackZone, is powered by automation, to constantly monitor your security level and help to solve issues as they arise with auto-remediations.
Use temporary credentials
Requiring identities to dynamically acquire temporary credentials will greatly reduce threats. You can use AWS IAM Identity Center (formerly AWS SSO) for workforce identities or federation with IAM roles to access AWS accounts. Implementing least privilege policies and removing unnecessary permissions are also excellent strategies. When it comes to machine identities, you should require the use of IAM roles instead of long-term access keys. Another useful resource when it comes to permissions is resource tags. You can use resource tags to control access to any AWS resources that support tagging and also tag IAM users and roles to control what they can and can’t access.
Continuously monitor your permissions and access levels
Nothing in the cloud should be fixed; your framework, chosen processes and your permission and access levels. As time passes, certain users will no longer require access to the same items so it’s up to you to ensure your identity and access management is up to date.
Next steps on AWS identity and access management best practices
To summarize, AWS identity and access management best practices are centered around maintaining visibility and control over your entire cloud infrastructure. It all starts with seeing the people who require access to your cloud environment as users, helping you install a zero trust policy. StackZone can help keep you in control of your cloud security with automation to help you effortlessly achieve the compliance standards of your industry. Book a demo and our team will show you how your cloud management will be transformed by StackZone.
This article was written by Fernando Hönig, Founder of StackZone
